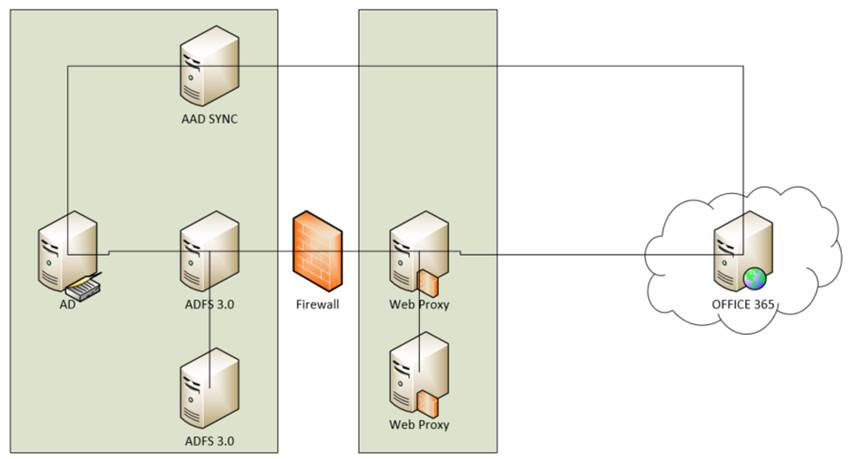
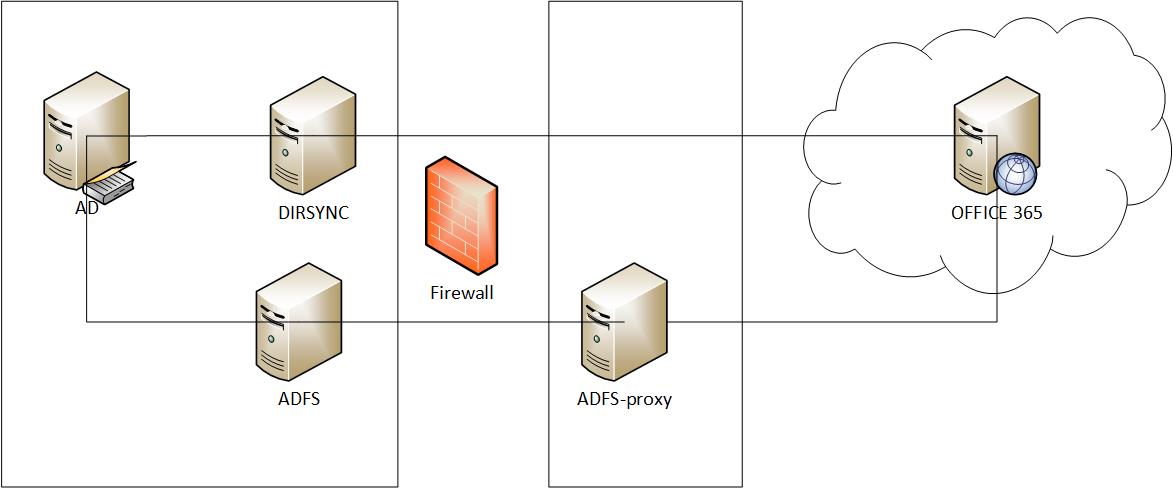
Om man vill synka användare från lokalt AD till Azure AD är det rekommenderat att använda AD Connect. Om man redan har användare i Azure AD vill man förmodligen mappa ihop dessa med lokala användare. Första gången man synkar mellan lokalt AD och Azure AD kommer AD Connect att försöka koppla ihop UserPrincipalName i AD med UserPrincipalName i Azure AD, en så kallad soft match. Ibland fungerar inte det av olika anledningar och då kan man själv göra denna mappning. Det gör man genom att skriva in ObjectGUID från AD i fältet ImmutableId i Azure AD. Dock måste man göra en base64-encoding på värdet först. Det går till ungefär så här:
$userPrincipalName = "myuser@powerkjell.com" adUser = Get-ADUser -Filter { userPrincipalName -eq $userPrincipalName } $guid = New-Object -TypeName System.Guid -ArgumentList $aduser.ObjectGUID; $immutableid = [System.Convert]::ToBase64String($guid.ToByteArray()); Set-MsolUser -UserPrincipalName $userPrincipalName -ImmutableId $immutableid |